It was a chilling morning when I discovered my Mercedes-Benz GLC 220 AMG Line Premium D vanished from my driveway. As a cybersecurity journalist with 18 years under my belt, I’d written extensively about car hacking, even interviewing luminaries like Charlie Miller. Yet, I’d fallen into the trap of believing “it won’t happen to me.” Suddenly, I was not just reporting on car theft, I was living it. This experience propelled me to delve deeper into the mechanics of modern car theft, particularly the role of readily available tools that exploit vulnerabilities within our vehicles, sometimes even through the seemingly innocuous On-Board Diagnostics (OBD) port.
The Alarming Rise of Car Theft: Beyond Smash and Grab
The UK’s car theft statistics are sobering. Recent DVLA figures reveal a car is stolen approximately every eight minutes. The Office for National Statistics paints an even starker picture, with 397,264 vehicles stolen in England and Wales between October 2022 and September 2023. Luxury brands like Land Rover and Mercedes-Benz top the list of most stolen vehicles, a dubious honor for manufacturers. Recovery rates hover around a dismal 20%, leaving many victims without their vehicles and facing significant disruption.
But these aren’t your grandfather’s car thefts. Gone are the days of shattered windows and hotwiring. My Mercedes, equipped with keyless entry and start, was stolen silently, leaving no trace of forced entry. Both keys were safely inside my home. The unsettling conclusion? My car was likely hacked.
Car Hacking or Relay Attack? Decoding the Terminology
“I’d say so, yes,” affirmed Graham Cluley, host of the Smashing Security podcast, when I described the theft. “In its broadest sense, hacking is gaining unauthorized access to something, and the scumbags who stole your car did just that, by exploiting a flaw in its entry system.” David Rogers, CEO of Copper Horse, a connected car security specialist, concurred: “It’s almost certainly car hacking.”
However, Adam Pilton, a former police officer and cybersecurity consultant at CyberSmart, offered a more nuanced perspective. While acknowledging the term “car hacking,” he suggested a “relay attack” as the most probable method, especially given that six similar vehicles were stolen in my vicinity over two nights. A relay attack, while technically simpler than complex code exploitation, is still a form of hacking – exploiting system vulnerabilities to gain unauthorized access.
Ivan Reedman of IOActive injects a critical point. He argues that while unauthorized access was gained, it wasn’t necessarily a “hack” in the traditional cybersecurity definition of accessing data within a system. He leans towards classifying it as theft leveraging technology, rather than a data breach.
Despite the varying definitions, the consensus among experts was clear: my car was stolen via a relay attack.
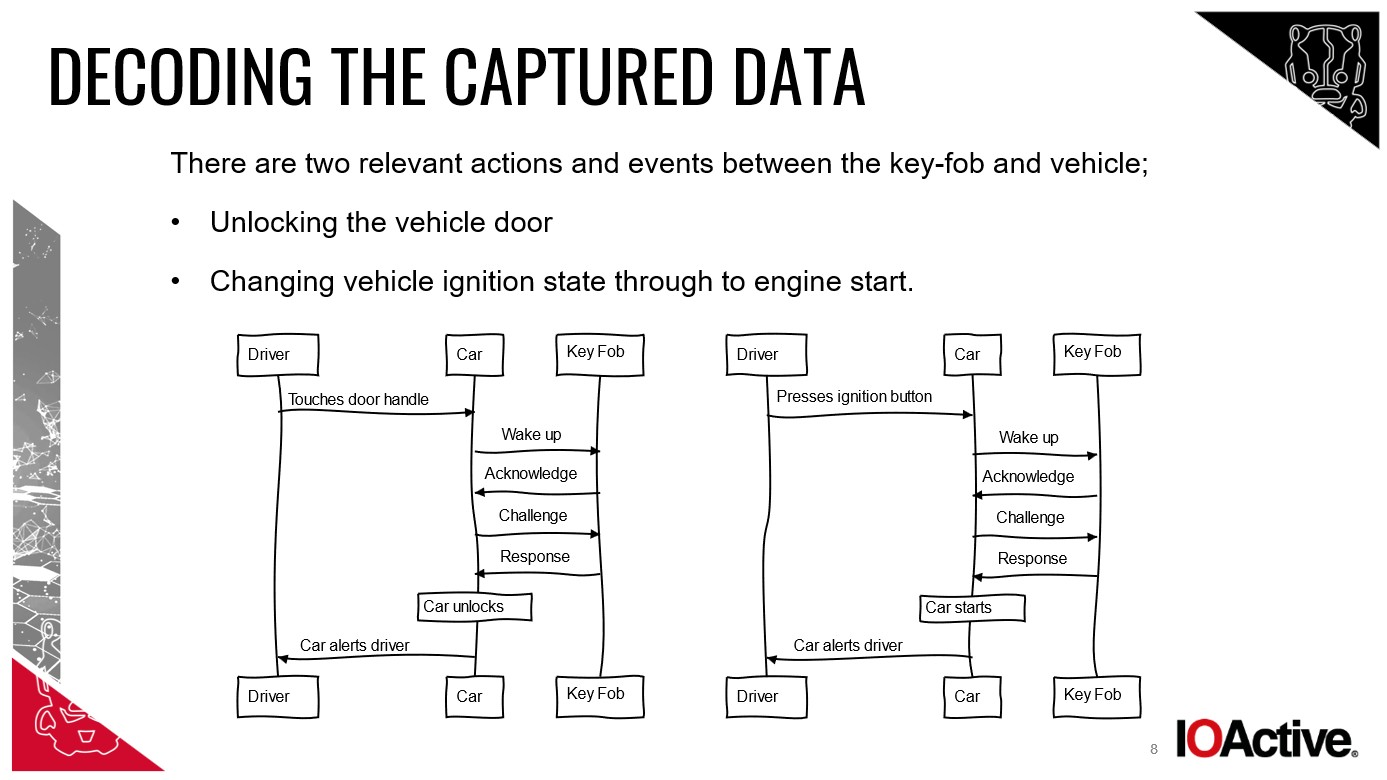
Relay Attacks: Amplifying the Keyless Vulnerability
My Mercedes featured Passive Entry Passive Start (PEPS). This convenient system allows entry and ignition as long as the key fob is nearby. Relay attacks exploit this convenience.
Chris Pritchard, a principal adversarial engineer at Lares, explained, “The thieves used a tool and aerial to relay the signal broadcast between your contactless key and the car. The car is tricked into thinking the key is close and unlocks the door.” William Wright, CEO at Closed Door Security, elaborated on the two-device setup: one near the house to capture the key fob signal, and another by the car to relay it. These devices need only be within 10-15 meters of the key and can execute the theft in as little as 30 seconds.
Illustration depicting the signal relay process in a keyless entry system attack.
Reedman, who demonstrated a relay attack using rudimentary equipment, emphasized the simplicity: “Relay attacks are one of the simplest attacks, requiring no [technical] knowledge or secrets.”
The crucial question remained: how did the thieves keep driving after the initial relay start? The answer lies in the OBD port.
OBD Port Exploitation: The Key to Long-Term Theft
While a relay attack starts the car, it doesn’t provide lasting control. Once the engine is running, most cars will warn of a missing key but won’t shut down for safety reasons. However, restarting the car without a legitimate key is usually impossible. This is where the OBD port becomes critical.
“Access to the OBD will trigger the car into starting by using other devices,” explains Rogers. The OBD port, typically located under the steering wheel, is designed for mechanics to diagnose issues and reset systems. Criminals exploit this port with readily available OBD programming tools.
Pritchard, drawing from his own experience of car theft, explained, “When my Audi was stolen…they broke in and programmed a new key with an OBD tool so they could open, close and start the car as needed. There’s a good chance something similar happened here.” These tools allow thieves to bypass security measures, program new keys, and potentially disable immobilizers, granting them full control over the vehicle.
While initially some suggested Flipper Zero or key cloning attacks, experts deemed them “highly improbable” in my case, reinforcing the likelihood of a relay attack followed by OBD exploitation.
OBD Tools: Readily Available and Dangerously Effective
The experts I consulted highlighted a disturbing reality: car theft equipment, including OBD programming tools and relay attack devices, is alarmingly easy to acquire. Rogers stated, “The majority of car thieves have no technical knowledge; they push a button on a box or wave an antenna, and the car unlocks.” The real expertise lies higher up the criminal chain, in those who develop and supply these tools.
Pilton added that these tools aren’t inherently designed for theft; they are often repurposed communication and signal extension devices. Reedman even downplayed the “hacking” aspect, stating, “It requires no skill. I suspect they do little more than watch videos online and buy the [relay] equipment. It’s trivial.” This ease of access and use is reflected in reports of even children being involved in car theft.
Manufacturer Response: Security Facelift and Customer Responsibility
With keyless car theft escalating, manufacturers are under pressure to enhance security. Mercedes-Benz, in their response, highlighted that from mid-2019, the GLC “facelift version received a motion sensor in the vehicle key. This means that as soon as the key does not move for a certain time, the KEYLESS GO function is deactivated. This also means that range extension is no longer possible.” My 2018 model, unfortunately, predated this upgrade.
They also mentioned the option to manually disable KEYLESS GO and the GUARD 360° ‘stolen vehicle help’ function, accessible via the Mercedes me app. However, the lack of proactive communication about these security options at the point of sale remains a concern.
Image depicting a modern car key, highlighting the technology susceptible to relay attacks.
Critics argue that manufacturers prioritize convenience over security, shifting blame onto owners by suggesting measures like Faraday boxes and steering locks. Rogers contends, “the negligence is on the manufacturer. They know about the issue with their vehicles, but they’re mostly not doing anything about it.”
Securing Your Keyless Car: Practical Steps
While manufacturers work on long-term solutions, car owners can take immediate steps to protect their vehicles. The overwhelming advice from experts centers on Faraday technology.
Cluley strongly recommends, “Use a Faraday box or wallet to block any signal being sent or received by your car keys and get into the habit of always putting your keys in such a box when you return home.” Reedman emphasizes testing your Faraday solution to ensure its effectiveness.
Beyond Faraday solutions, Rogers suggests disabling keyless ignition if possible, using mechanical steering locks, and even considering OBD port locks to physically secure this vulnerable access point. Pilton highlights the importance of raising awareness through social media and community sharing.
The Road Ahead: Legislation and Shared Responsibility
The UK’s Criminal Justice Bill aims to criminalize the possession of electronic devices used for vehicle theft, including signal jammers. However, concerns exist within the security research community about its potential impact on legitimate security research.
Ultimately, preventing car theft requires a multi-faceted approach. Manufacturers must prioritize security in design and actively educate consumers. Law enforcement needs to target organized crime and the supply chains of theft tools. And car owners must adopt proactive security measures.
My personal experience has transformed me from a detached observer to a vocal advocate for car security awareness. While “dumb cars” might seem appealing in retrospect, the reality is that technology is integral to modern vehicles. The focus must shift to making this technology secure and empowering car owners to protect themselves in an increasingly connected world. Understanding how OBD tools and relay attacks are exploited is the first step towards unlocking better car security for everyone.